Ring-1 openly boasts about how their security is impenetrable and how no one has ever cracked them before. That’s changed. Over the course of the past 6 months and the last year and a half that I personally worked for them me and some friends personally found, broke, and exploited their system from the inside unbeknownst to them for months.
First let’s start off with how we did it.
I previously worked for ring-1 and with that we had limited access to the admin panel. As [support] you were able to view support tickets, the user database (username, email, ip, etc) but not a ton of info. So like anyone I started doing some snooping. Nothing crazy at first just looking at moderator emails and whatnot. Some people were more secure and used @protonmail emails with no relation to their IRL self. But others weren’t careful at all.
What got us into a higher version of the panel was Overpowered’s account. He used his regular gmail account. Put that email into Snusbase and there we have his common password.
No surprise, that actually worked to login. And if you login directly through the admin panel it doesn’t alert the user (great design)
Through using the SQL toolbox present within the AdminCP we were able to take control of an inactive admin account under the name “Blitzz” this account would be very useful in the near future. By securing this account we were able to use the account if the previous account was taken back.
UPDATE core_members set email = '@protonmail.com' where name = 'username'
And we did so with old accounts from 2019 so that they would go undetected for months without being in the recent users.
Throughout the 6ish months where we had access to the panel we generated over $20,000 worth of account credit whether it be for personal use or for sale
Further income was generated from having access by selling access to the DB as passwords were stored in MD5 hashes and all personal info was in plaintext.
UPDATE core_members set cm_credits = '{"EUR":"5000.00"}' where name = 'turn'
We did definitely figure out how to send gift cards to other users though
{"method":"email","recipient_email":"test@protonmail.com","recipient_name":"lol","sender":"admin","message":"hehe boi","amount":500,"color":"#16a085","currency":"EUR","code":"7148X9840XPR1H7B9EHP"}And the recipient was able to take that code and apply it to the store and it would give them that amount.
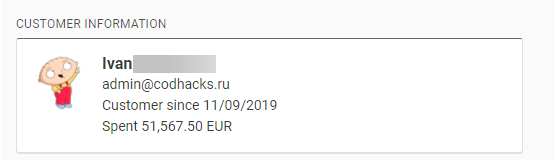
We were even able to see how much a user has spent onsite
We also were able to cover our tracks by deleting login times and logs from the database through the SQL Toolbox. The most efficient way being through whatever VPN IP we were logged into at the time. Though some of us took advantage of Brave Browser’s Tor feature.
DELETE FROM core_admin_logs WHERE ip_address = '1.1.1.1'And we deleted invoices from friends that we knew so that they couldn’t be looked at later.
DELETE FROM nexus_invoices WHERE i_id = 123456
As we had access to the DB we were able to change information about accounts as we modified the information stored on the account

Ring-1.io boasts about their security but their entire website was vulnerable to attack such as CWE-434 (not a joke) allowing for us to execute .php scripts through avatar upload. By abusing this we were able to gain more information about the site furthering our penetration of it
As we had control over Overpowered’s account we were able to change account credentials.
The video shows us swapping an accounts password just by changing a single hash within the DB. This was used on numerous occasions against resellers, inactive accounts and the admin account.
Ring-1.io claims to be uncrackable but here is the exploit chain they use to inject their cheats, in a simpler format they store the internal cheat inside of their hyper-v payload and the loader is used to decrypt it/payload is used to inject & spoof cr3 reads, which in turn is stored inside of the bootmgfw.efi they swap on disk (they restore bootmgfw.efi during boot/before the windows kernel takes control/any windows boot drivers get loaded and running)
Credit to: _xeroxz for the Hyper-V research
Follow his twitter

When someone created a support ticket stating their was an exploit within the site allowing for infinite credit they dismissed it but soon realised that there was someone with access to the admin control panel but had no idea how even though they created “uncrackable software”
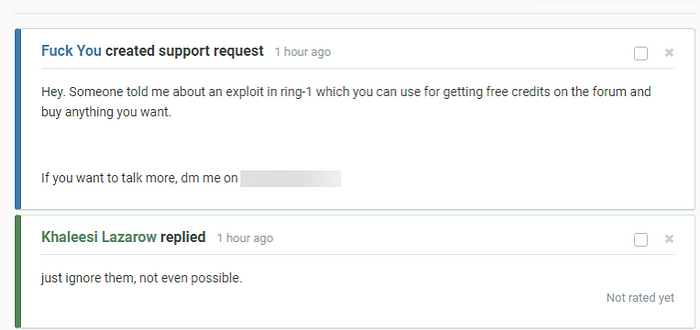
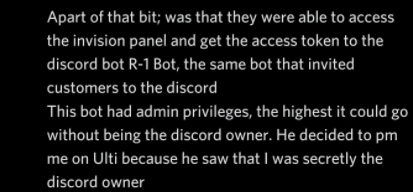
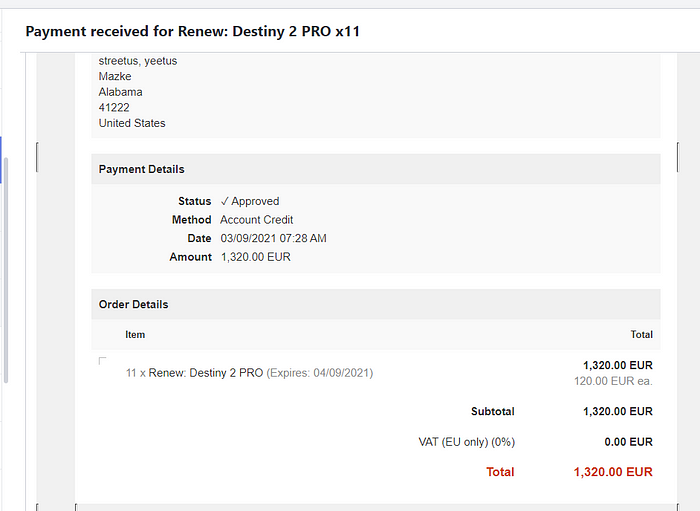
Here is proof of our past claims of having access to unlimited account credit, This user was banned months before we were discovered but maintained that he found an exploit within the gift card system aiding us in being able to keep going, it led to Overpowered begging the user for how he obtained the credit
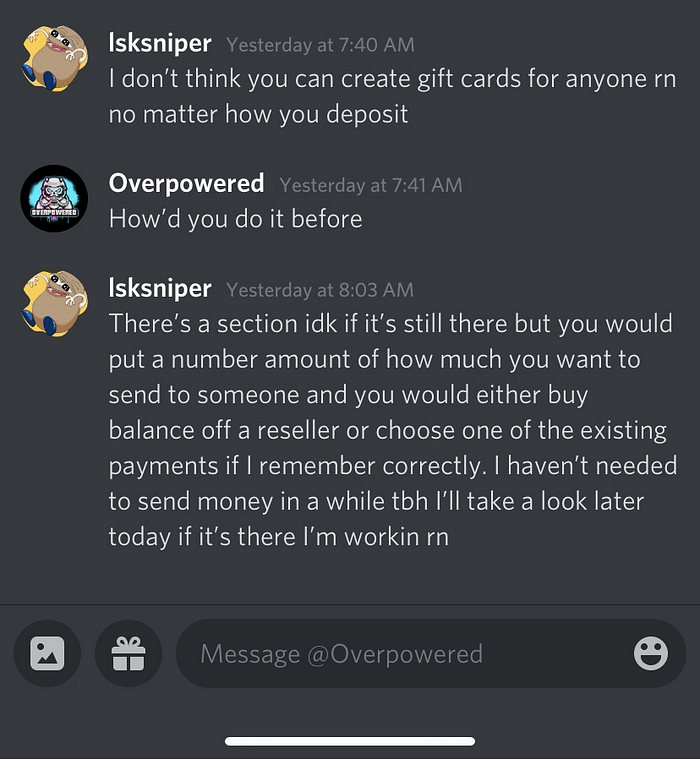
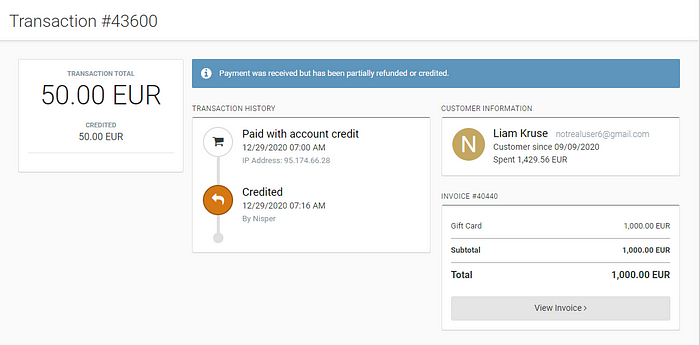
R1 hires top tier coders, I was told in january about an update coming to the loader that would change the injection method. This was swapping out the directx driver with their own. Leaving no traces of the change. But 6 months later they still havent even put it into testing. Presumably because all of R1s “super” features being pasted from other cheats that they’ve cracked or purchased themselves.
Examples of that being their updated Destiny 2 cheat, when PerfectAim was C&D by Bungie and sold to GatorCheats they took some of the code Gator implemented and added speed, noclip, PVE ESP, fly, and OPK. In their Cold War cheat the XP features for the “PRO” version of the cheat came from HyperHaxz’s Lobby Tool, cracked and added into R1’s cheat.
Talking about cease & desists Overpowered and Krypto (the old moderators) received several from Activision. Their response to this was to swap aliases, Krypto went to Cypher and Overpowered went to Beserker.
“i didn’t get told to change my name xD i got somewhat of a cease and desist Soo.. Krypto going back to Krypton xD and Cypher is coming out to play” — Krypto”
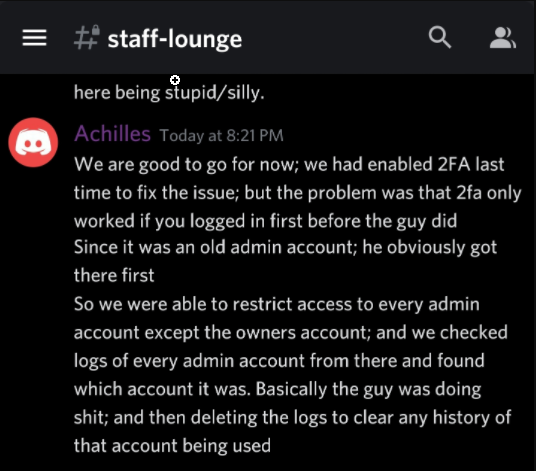
Times we thought we were caught we actually managed to get away unscathed until last week. Crazy thing is, they added all of these things so that no one could login as someone else like using Google Authenticator. Fortunately, we were faster. The admin account that we had email swapped with the database access we logged into, added GoogleAuth (changed the email back to the original but recreated it on protonmail), and then logged back out. Up until March 2021, we had full admin access.
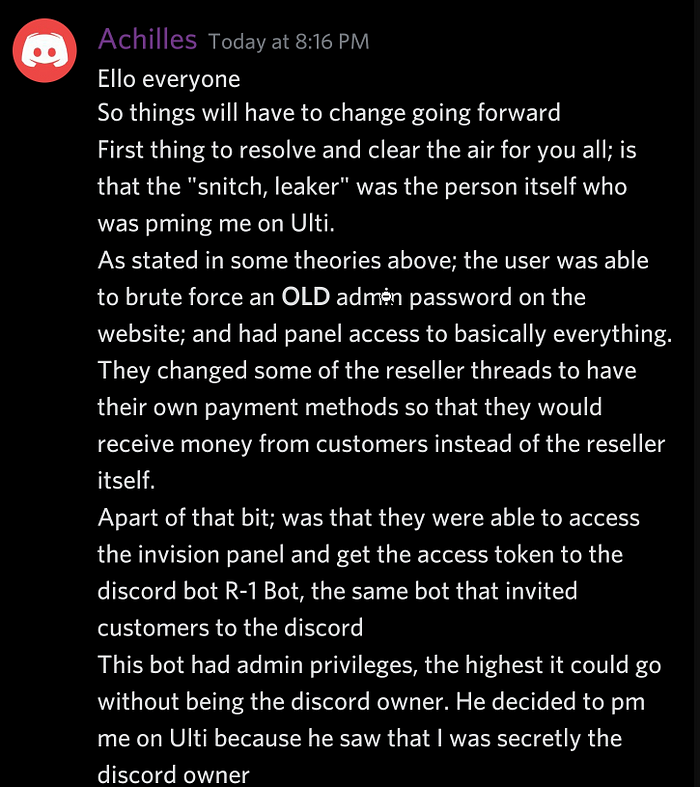
The “bot” in question here is our using the database access to log into the Ring-1 Discord bot through its token.
You’re a gaming company and want to detect R-1 because they actively talk about how many of their cheats haven’t been touched since release? Here’s how:
Due to a flaw within the exploit a copy of Hyper-V and the payload are floating around in reclaimable memory. If you translate the virtual address of the Hyper-V allocation during boot then map that physical memory with MmMapIoSpace you will be able to dereference it
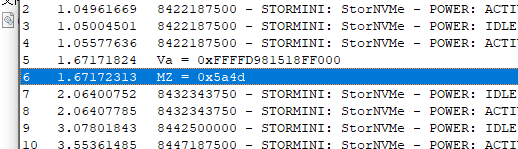
As a final comment, nothing is “uncrackable”, sometimes it’s pretty simple.
